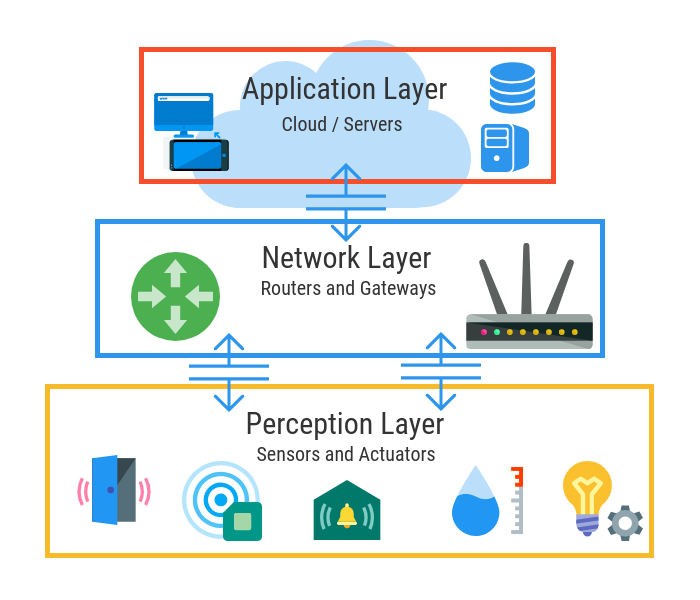
Architecture Of IOT :
There is no single and general agreement about the architecture of IoT that is agreed on by the whole world and researchers. Many and different architectures have been proposed by researchers. According to some researchers, IoT architecture has three layers, but some researchers support the four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed architecture can fulfill the requirements of IoT regarding security and privacy.
.
Perception layer :
It is also known as a sensor layer. It works like people's eyes, ears and nose. It has the responsibility to identify things and collect the information from them. There are many types of sensors attached to objects to collect information such as RFID, 2-D barcode and sensors. The sensors are chosen according to the requirement of applications. The information that is collected by these sensors can be about location, changes in the air, environment, motion, vibration, etc. However, they are the main target of attackers who wish to utilize them to replace the sensor with their own. Therefore, the majority of threats are related to sensors [35-37]. Common security threats of perception layer are:
Eavesdropping:
Eavesdropping is an unauthorized real-time attack where private communications, such as phone calls, text messages, fax transmissions or video conferences are intercepted by an attacker. It tries to steal information that is transmitted over a network. It takes advantage of unsecure transmission to access the information being sent and received.
Node Capture:
It is one of the hazardous attacks faced in the perception layer of loT. An attacker gains full control over a key node, such as a gateway node. It may leak all information including communication between sender and receiver, a key used to make secure communication and information stored in memory [38].
Fake Node and Malicious:
It is an attack in which an attacker adds a node to the system and inputs fake data. It aims to stop transmitting real information. A node added by an attacker consumes precious energy of real nodes and potentially control in order to destroy the network.
Network layer:
Network layer is also known as transmission layer. It acts like a bridge between perception layer
and application layer. It carries and transmits the information collected from the physical objects
through sensors. The medium for the transmission can be wireless or wire based. It also takes the
responsibility for connecting the smart things, network devices and networks to each other. Therefore,
it is highly sensitive to attacks from the side of attackers. It has prominent security issues regarding
integrity and authentication of information that is being transported in the network. Common security
threats and problems to network layers are:
• Denial of Service (DoS) Attack:
A DoS attack is an attack to prevent authentic users from accessing
devices or other network resources. It is typically accomplished by flooding the targeted devices
or network resources with redundant requests in an order to make it impossible or difficult for
some or all authentic users to use them [41].
• Main-in-The-Middle (MiTM) Attack:
MiTM attack is an attack where the attacker secretly
intercepts and alters the communication between sender and receiver who believe they are
directly communicating with each other.
Since an attacker controls the communication, therefore
he or she can change messages according to their needs. It causes a serious threat to online
security because they give the attacker the facility to capture and manipulate information in real
time [42].
• Storage Attack:
The information of users is stored on storage devices or the cloud. Both storage
devices and cloud can be attacked by the attacker and user’s information may be changed to
incorrect details. The replication of information associated with the access of other information by
different types of people provides more chances for attacks.
• Exploit Attack:
An exploit is any immoral or illegal attack in a form of software, chunks of data or
a sequence of commands. It takes advantage of security vulnerabilities in an application, system
or hardware. It usually comes with the aim of gaining control of the system and steals information
stored on a network [43].
Application Layer:
Application layer defines all applications that use the IoT technology or in which IoT has deployed.
The applications of IoT can be smart homes, smart cities, smart health, animal tracking, etc. It has
the responsibility to provide the services to the applications. The services may be varying for each
application because services depend on the information that is collected by sensors. There are many
issues in the application layer in which security is the key issue. In particular, when IoT is used in
order to make a smart home, it introduces many threats and vulnerabilities from the inside and outside.
To implement strong security in an IoT based smart home, one of the main issues is that the devices
used in smart homes have weak computational power and a low amount of storage such as ZigBee [44].
Common security threats and problem of application layer.
• Cross Site Scripting:
It is an injection attack. It enables an attacker to insert a client-side script,
such as java script in a trusted site viewed other users. By doing so, an attacker can completely
change the contents of the application according to his needs and use original information in an
illegal way [45].
• Malicious Code Attack:
It is a code in any part of software intended to cause undesired effects
and damage to the system. It is a type of threat that may not be blocked or controlled by the use
of anti-virus tools. It can either activate itself or be like a program requiring a user’s attention to
perform an action.
• The ability of dealing with Mass Data:
Due to a large number of devices and a massive amount of
data transmission between users, it has no ability to deal with data processing according to the
requirements. As a result, it leads to network disturbance and data loss.
There is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacy
There is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and privacyThere is no single and general agreement about the architecture of IoT that is agreed on by the
whole world and researchers. Many and different architectures have been proposed by researchers.
According to some researchers, IoT architecture has three layers, but some researchers support the
four-layer architecture. They think that, due to enhancement in IoT, the architecture of three layers
cannot fulfill the requirements of applications. Due to a challenge in IoT regarding security and
privacy, the architecture of five layers has also been proposed. It is considered that a recently proposed
architecture can fulfill the requirements of IoT regarding security and p